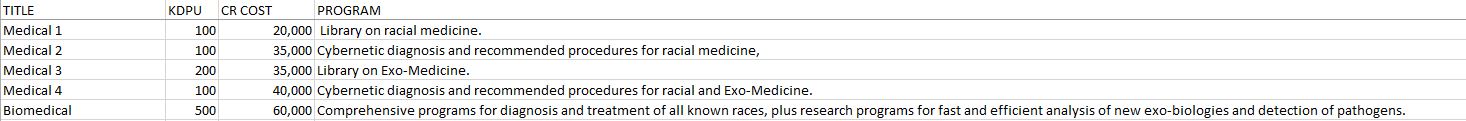Future Imperfect - Starship Software
Contents
[hide]Routine Procedures
Library
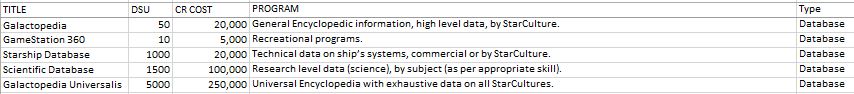
Much of the detailed information concerning the known universe is contained in the encyclopedic information program, and these are regularly consulted by crew and passengers. It should be noted that some information will be incomplete or in error, even non-existent. Technical data (Library 3) is essential for significant repairs to damaged ship’s systems to be performed. Research data (Library 4) contains highly detailed information on a variety of scientific disciplines which would be required to undertake serious research. The Universal Encyclopaedia (Library 5) contains all of the basic knowledge of the race (to its Tech level), and military and survey ships have highly classified data as well, under coded need-to-know and even self-destruct interlocks to prevent unauthorized access. Technical programs tend to be very accurate and are regularly employed by Science Officers, Astrogator's, Engineering Officers, etc., in the course of their duties. In any case, the chance of error or incompleteness of information must be decided by the StarMaster as is appropriate to the situation and the nature of the questions asked of the computer. Retrieval time: variable, from seconds x computer speed to days.
Ship’s Systems
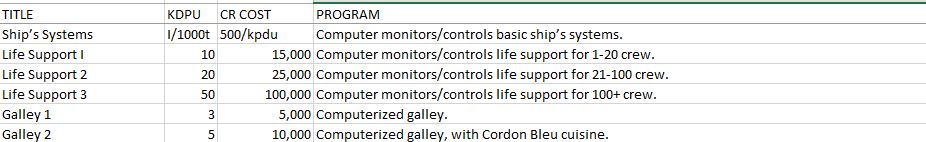
Routine programs to monitor and regulate the many secondary systems aboard ship, illumination, automatic doors, etc.
Life Support: Program to monitor and regulate the internal temperature, atmospheric pressure and composition, hydroponics and emergency systems, etc. When running in tandem with a medical program, it is possible to monitor the life responses of each person fitted with biomedical telemetry. Life support programs are not essential, but their absence requires a crewman to maintain regular watch and adjust the systems when required.
Galley: Programs which operate automated galley facilities and which also contain recipe libraries. Galley 2 will have not only racial recipes for haut cuisine but also information on the preparation of alien foods—essential to passenger vessels carrying a variety of races.
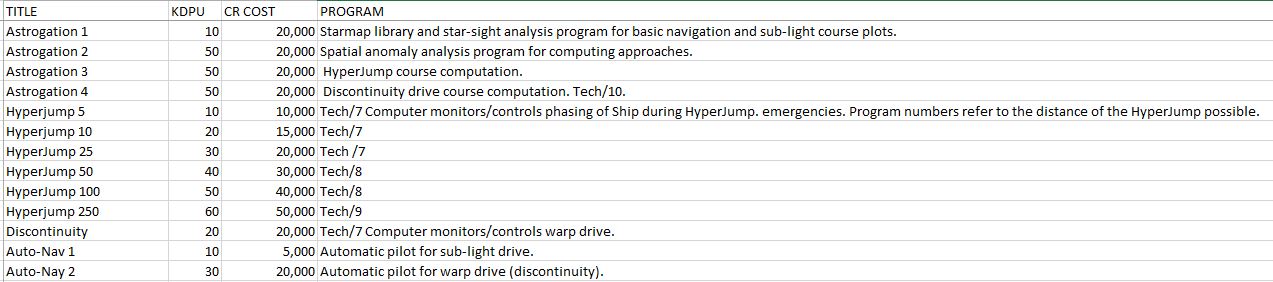
Astrogation: A series of programs required to plot courses and manually navigate the vessel under various conditions. Setting courses may require computer speed x seconds, minutes, or hours, depending upon the nature of the procedure. Known courses are retrieved almost instantly from the memory banks, as are standard maneuvers.
HyperJump: Programs which are run simultaneously with Astro 3, interfacing the course program with the phase-shift generators to take the ship to the plotted destination. A HyperJump program is merely the control program and must be directed by the course figures fed into it. Manual course directions are possible (in case of a malfunction of Astro 3), but course setting will take many hours as a program must literally be written by the Astrogator.
Discontinuity: Program which is run simultaneously with Astro 4, interfacing the course program with the warp-drive units to produce the discontinuity field which places the ship slightly out of phase with the normal space-time continuum and so permits FTL speeds.
Auto-Nav: Auto-pilot programs permitting the main computer to con the ship. When interfaced with a simultaneously running Auto-Evade program, Auto-Nav will make course corrections to avoid objects in space, etc.
Operations
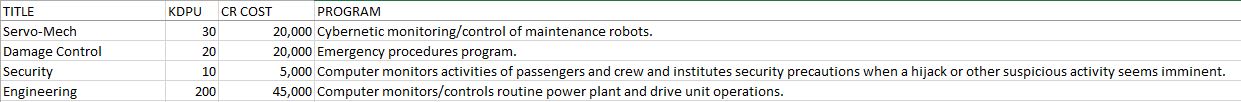
Servo Mech: Program to monitor and direct cybernetised maintenance systems and robots. Such systems are typically found on large vessels, but may be installed on small ships as well to reduce crew and increase safety.
Damage Control: Emergency procedures program automatically activated whenever any of the ship’s systems malfunction or the ship is hulled, and the lives or safety of the crew and passengers are endangered. Closing of air-tight doors, emergency alarms, activation of backup systems, alerting of Servo-Mech systems, etc., are included in this program.
Engineering: Program to monitor and control routine power plant and drive unit operation, with technical data interface with Library 3, Ship’s Systems, Life Support, Servo-Mech, and Damage Control programs, as required. Mandatory program on all Starships.
Security: An internal security program which monitors suspicious activities and automatically locks doors and imposes coded interlocks on key systems when a hijacking or other related action seems apparent. Such measures can be thwarted by rolling 1d6 and obtaining a result of 1 or 2.
Survey Procedures
Stellar Analysis: Program to analyse spectrographic and other astronomical data about a particular star. Retrieval time = computer speed in minutes. When running simultaneously with an Astrogation program, bright marker stars are automatically analysed and compared to data on known stars in the memory bank for identification--most useful in finding out the position of the ship after an Anomaly Jump or HyperJump has resulted in the ship’s becoming lost.
Planetary Survey: Program to analyse sensor and visual data to determine basic planetary conditions from the ship while in orbit or when grounded. Local data may also be transmitted for computer analysis by landing parties. Some error is likely during initial observation, but as data is collected over time, accuracy increases significantly. Retrieval time = computer speed in seconds, minutes, or hours, depending upon the type and complexity of the questions posed for analysis, and whether data is already stored in the memory bank. Astronomical Survey: Program to chart the major bodies in the star system, compute orbits, orbital speeds, distance from primary, etc. Retrieval time = computer speed in hours (to account for astronomical scanning time). Known systems have retrieval time in seconds.
Comparative Cultures: Contact program to analyse alien cultures. The program is regarded as essential by Contact Officers, who must recommend procedures for approaching unfamiliar cultures. For example, the program requires Library 5 to reach reasonably accurate results, while Library 1 is too general to produce more than a sketchy analysis (often inaccurate or incomplete in many respects). Library and Comparative Culture programs must be run simultaneously for analysis. Retrieval time = computer speed x hours or days, depending upon the amount of data on known races is a matter of seconds or minutes, depending upon the completeness of the read-out.
Linguistics: Contact program to analyse alien languages. For analysis, the program requires Library 5 to be accurate, while Library 3 will not produce more than a basic vocabulary of several hundred words and phrases. Retrieval time computer speed x hours for basic speech: computer speed x days or weeks for fluent speech. It is assumed that sufficient data (in the form of actual alien speech patterns and tangible referents for comparison to racial language equivalents) has been acquired to permit accurate translation into familiar symbolisation. Furthermore, some alien races have concepts and behavioural requirements so alien to others that translation of some elements of the language will prove impossible over the short term. Speech patterns derived from known languages (say, the language of a ‘lost’ colony speaking a variant of Ancient Anglish) can often be analysed in minutes. Once a language has been decoded, simultaneous computer translation is possible.
EcoSystem Survey: A highly complex program to analyse and provide extrapolations of possible life form and their relationships in the planetary environment. The program requires preliminary data from a Planetary Survey and must be run simultaneously with a Library 5 program to interface all known data with the data obtained on specimens gathered and observed on the new planet’s surface. Depending on the range of specimens found, the depth of the problem set, and the accuracy of data obtained, retrieval time = computer speed x minutes, hours, days, weeks, or even months. Generally, preliminary analysis of a particular life form is possible in minutes. More complex problems take longer. Where known planets are involved, retrieval time is in seconds. StarMasters should work in some degree of inaccuracy or incompleteness when answering, especially in the earlier stages of the survey. Further, when interfaced with a Medical 5 programs, detailed analysis of micro-organisms, etc., can be made. Sensor Probe: A program which analyses data and provides chemical and physical analysis of the ‘target’ or subject of the probe. When interfaced with the ship’s Library 5 program, known objects or beings can be analysed with great accuracy, and biomedical data can be obtained by interfacing with medical program.
Biomedical Procedures
Medical I: Standard reference library on all significant aspects or racial medicine.
Medical 2: Program to monitor/regulate computerized medical systems and, when interfaced with Medical I programs, to make diagnoses and recommendations for treatment.
Medical 3: Standard reference library on significant aspects of exomedicine.
Medical 4: Program resembling Medical 2. except with application to alien life forms on which data has been acquired.
Medical 5: Comprehensive programs which, when interfaced with Medical 1/2/3/4, will provide detailed diagnosis and treatment procedures for all known life forms; regulate and monitor automatic medical support systems; operate cybernetised surgeries, pharmacies, and culture labs; and conduct computer research on a wide variety of medical subjects. When interfaced with EcoSystem programs, detailed analysis of pathogens may be performed.
Retrieval times will vary. Generally, routine procedures on known life forms will produce answers in seconds. Diagnosis may require significantly longer periods, depending upon the symptoms and the illness itself. Research may take considerable time.
Battle Procedures
Situational Analysis
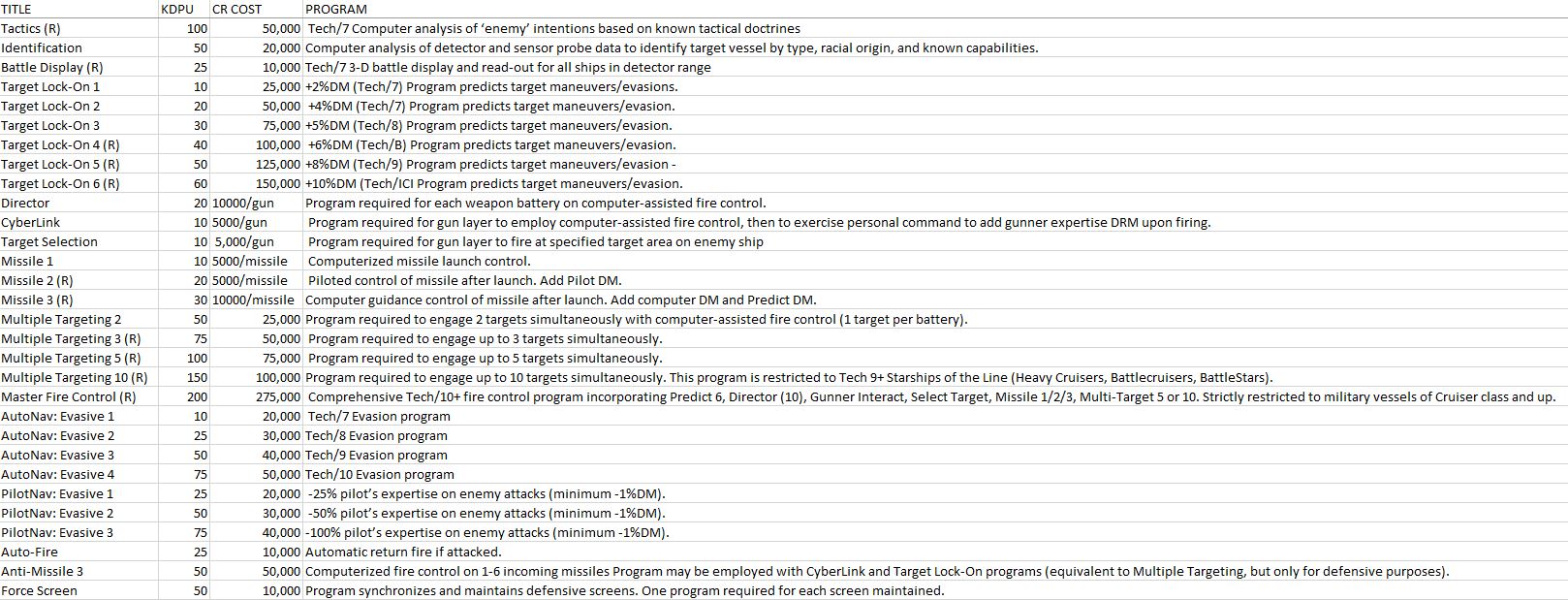
Tactics: A restricted program reserved for military use, but which may be obtained by commercial vessels venturing into dangerous regions of space (upon passing a rigorous security check). The program contains data on all known tactical doctrines of races with which contact has been made or hostility has been encountered. When engaged, the program can assess with a high degree of probability the likely intentions of a ship from its maneuvers. When engaged, the program enhances offensive and defensive capability. Identification: A program containing all known configurations of ships with which contact has been made or hostility has been encountered. It is routinely engaged whenever the detectors reveal the presence of a ship within detector range. Enemy vessels so identified produce an automatic alarm. Battle Display: A restricted program reserved for military use. A holographic 3-D display presents the region around the ship in a ‘battle tank,’ with full read-outs on speeds, courses, power maneuvers, defensive screens, apparent armaments, and identification of type and, racial origin. The system can also be used to identify asteroids, etc., within detector range. The program must be interfaced with Tactics and Identification, and is essential to the operation of Multiple Target 5/10 or Master Fire Control programs. Rarely is it employed on ships of less than Light Cruiser class. Offensive/defensive capability is enhanced when the program is engaged.
Offensive Action
Target Lock-On: A series of programs which analyze courses, maneuvers, and evasions of vessels in order to predict their future positions and so permit accurate fire control. Target Lock- On 1/2/3 programs are generally available, but Target Lock-On 4/5/6 programs are restricted to the military. When interfaced with Tactics and Battle Display programs, DMs for Tactics and Battle Display may be added to Target Lock-On DMs. Full Target Lock-On DMs are added to energy weapon hit probabilities, Missile 2/3 programs. Missile 1 programs add ‘A the DRMs for Target Lock-On (rounding fractions down) if target is evading. Director: A gunnery direction program which is required for each weapons battery on computerized fire control (Target Lock-On). Six batteries, for instance, would require six programs, as fire is by salvo to ‘bracket’ the target. When more than 10 batteries are involved, 10 programs will provide control.
CyberLink: A program allowing the gun layer of a weapon battery to interface his own expertise with computerised fire control.
Target Selection: A program allowing the gun component of a weapon battery to aim at a specific section of the target, but with reduced chances of hitting. Only PC gunners under independent control may use this rule. Critical hits penetrating the hull will strike sections aimed at.
Missile: A series of programs to effect control of missile launches. Missile 1 is comparable to launching torpedoes, and full Target Lock-On DRMs are applicable only if the target fails to evade. Missile 2 is a program requiring a pilot to guide the bomb once it has been launched, bringing pilot expertise and full Target Lock-On DMs into play, and also permitting evasive maneuvers to avoid anti-missile fire. Only the largest and most sophisticated missiles may be piloted. Missile 3 is a program requiring a computer to guide the bomb after launch, with full Target Lock-On DMs being added to its hit probability. Using Missile 1, a maximum spread may be fired. Missile 2 and 3 permit control of 2 missiles under guidance.
Multiple Targeting: A series of programs permitting computerized fire control to engage more than one target. Each weapon battery may engage only a single target, but the computer can handle fire Control data to direct fire at as many targets as specified by its program number Master Fire Control: A program incorporating Tactics, Identification, Battle Display, Target Lock-On 7/8. Director (10+ batteries), CyberLink, Target Selection, Missile 1/2/3, Multiple Targeting 10, Auto-Fire (see Defensive Procedures), and Anti- Missile (see Defensive Procedures). Tactics/Identification/Battle Display are always operational at CDPC 4 and will automatically sound Battle Stations on detection of hostile ships or potentially unfriendly maneuvers, and the ship will be brought to instant readiness or computer control. ECM and Force Screens may also be interfaced. The ship will engage on computers, if required, if the crew has not closed up to battle stations. Such systems are generally reserved for Heavy Cruisers, Battlecruisers and BattleStars.
Action
AutoNav: Evasive: An auto-pilot program series which must be interfaced with a simultaneously running AutoNav program for computer control, or else which may be engaged with a PilotNav: Evasive program to augment the pilot’s evasive maneuvers.
PilotNav: Evasive: A series of programs run when a pilot has direct control of the ship and is maneuvering or evading enemy fire.
Auto-Fire: A program which instructs the computer to immediately return fire on any ship opening fire on its vessel. The program is used to provide defensive fire against incoming missiles or else offensive fire against an attacking ship, depending crew reaction.
Anti--Missile: A program permitting full computerized fire control on I, 2, or 3 incoming missiles. The program may be interfaced with Gunner Interact and Predict programs, but is designed to range missiles and cannot be employed as an offensive Multi- Target program. On the other hand, Multi-Target programs may function as Anti-Missile programs.
Force Screen: Program to monitor and control force screen operation. Often, the program is immediately activated when an unidentified ship comes into detector range. ECM 1: Electronics counter-measures program which ‘blinds’ enemy detection apparatus somewhat and reduces their gunnery accuracy. Several ECM programs (up to 3) can be run simultaneously, but the gunnery of one’s own ship is reduced when 2 or 3 are engaged.
ECM 2: Electronics counter-measures program which causes from 2 to 6 ‘echoes’ to appear on enemy detector screens, with appropriate reduction in their gunnery. If more blips appear than are in the enemy’s Predict programs number, the differences is added to the defensive DM. For example, suppose 5 ‘echoes’ are created and the enemy’s Predict program is No. 3. The defensive DM = 10% (number of echoes) + 5% (Predict 13) = -5%. However, if the enemy also has the system, he may employ it as an electronic counter-measure to penetrate the deception by rolling 1-6 on a 06 and subtracting his total from the defenders DMs. (Unless already activated, this counter-program must be activated in the following battle turn).
ECM 3: Electronics counter-measures program which jams enemy communications channels. It is effective according to the difference in EW levels, with a minimum probability of 1 per level of superiority. Roll 1d10. The number equal to or lower than the difference in EW levels = effective communications jamming. For example, if Tech difference is +2, 1 to 3 must be rolled. The minimum is always 1 chance in. 10. The counterjamming program works in the same way, with superior EW systems always having the advantage.